Brute force password
Data: 4.03.2018 / Rating: 4.8 / Views: 916Gallery of Video:
Gallery of Images:
Brute force password
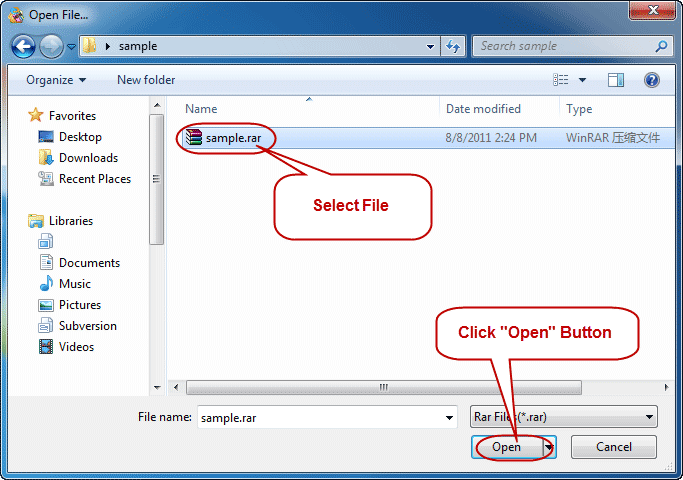
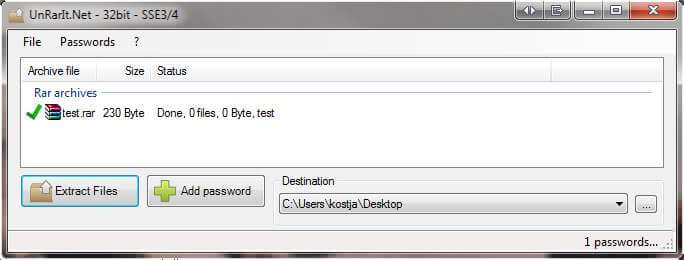
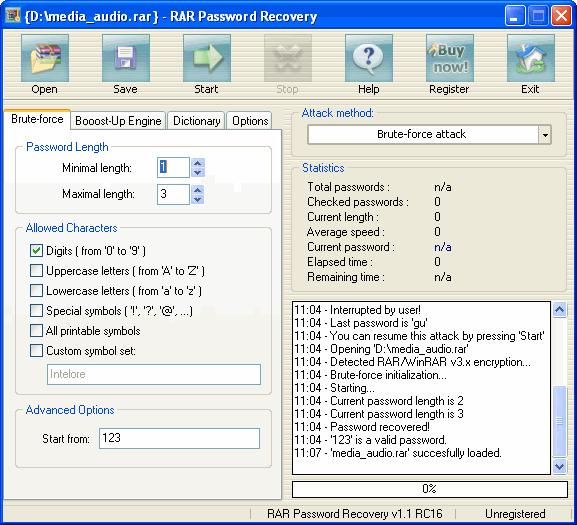
Is possibile to recover a forgotten password about a Microsoft Office file using automation? The answer is yes, by the brute force via automationInterop, the multithreading and a lot of quantifiable cpu time. The main goal of this software is verify the capability of Interop to open the password. brute force password attack My SBS 2003exchange event viewer security logs shows many logon attempts using random userids and it is always using PID of inetinfo; Logon type is 3, logon process is Advapi, and Source Network is always blank. Brute force attacks are carried out by hackers who try to crack a password by simply trying out different combinations of characters in quick succession. Short Bytes: Password cracking is an integral part of digital forensics and pentesting. Keeping that in mind, we have prepared a list of the top 10 best password cracking tools that are widely. Download BruteForcer for free. A clientserver multithreaded application for bruteforce cracking passwords. The more clients connected, the faster the cracking. Brute force cracking is method used by application programs to crack encrypted data, such as passwords or Data Encryption Standard (DES) keys, through exhaustive effort (using brute force) rather. Bruteforce attacks are simple to understand. An attacker has an encrypted file say, your LastPass or KeePass password database. They know that this file contains data they want to see, and they know that theres an encryption key that unlocks it. A brute force attack is also known as brute force cracking or simply brute force. Techopedia explains Brute Force Attack One example of a type of brute force attack is known as a dictionary attack, which might try all the words in a dictionary. The bruteforce attack is still one of the most popular password cracking methods. Nevertheless, it is not just for password cracking. Bruteforce attacks can also be used to discover hidden pages and content in a web application. THC Hydra is very prominent online bruteforce tool and has been featured in NullByte quite a lot. It is dictionary based, as you will have to provide a wordlist with possible passwords. WonderHowTo Null Byte How To: Audit remote password using THCHydra 34 Comments 1. facebook brute force free download. True Brute Force Tool This program works on everything that has a password. Takes 5 minutes to crack a 3 character passwor remember me reset password. netsecstudents subscribe unsubscribe 33, 326 readers. Best Wordlist for brute force attacks? submitted 4 years ago by EagleClaw322. In cryptanalysis, a brute force attack is a method of defeating a cryptographic scheme by trying a large number of possibilities; for example, exhaustively working through all possible keys in. Ophcrack is a free Windows password cracker based on rainbow tables. It is a very efficient implementation of rainbow tables done by the inventors of the method. It comes with a Graphical User Interface and runs on multiple platforms. Bruteforce module for simple passwords. The term brute force means to overpower the defense through repetition. In the case of password hacking, brute forcing involves dictionary software that recombines English dictionary words with thousands of varying combinations. (Yes, much like a Hollywood safecracker movie. Every password you use can be thought of as a needle hiding in a haystack. After all searches of common passwords and dictionaries have failed, an attacker must resort to a brute force search ultimately trying every possible combination of letters, numbers and then symbols until the combination you chose, is discovered. Is there a brute force password cracking software that you guys prefer? It doesnt have to be free but i do need it to be able to Try to find the password of a file that was encrypted with the 'openssl' command. Finally, a burp intruder bruteforce attack of passwords, with the th entry being the correct password passwd, confirmed the trivial bruteforce attack: Logging in with the harvested credentials again worked, no account lockout or other security controls. Online password Bruteforce attack with Hydra Tutorial, password attacks, Online attack, hacking tutorial, hacking news, Kali tutorial Online Password Bruteforce Attack With THCHydra Tool. BALAJI N October 17, 2017 StegCracker Bruteforce Utility to Uncover Hidden Data Inside Files. Thanks to the highly optimized lowlevel code, Advanced Archive Password Recovery provides the bestinclass performance for the bruteforce password recovery, attempting millions different password combinations per second on a typical ZIP archive with a modern CPU. Official info for the 2018 BRUTE FORCE 750 4x4i EPS specs, photos, videos, brochure reviews. Find dealer inventory, schedule a test ride get a quote. We will send you an email that will allow you to reset your password. An email will be sent to you shortly. No account found with that email address. Brutus is one of the fastest, most flexible remote password crackers you can get your hands on it's also free. It is available for Windows 9x, NT and 2000, there is no UNX version available although it is a possibility at some point in the future. This carries inference that 7Zip password encryption is one of the strongest between popular encryption systems in the context of brute force rate. Features Advantages of cRARk for 7Zip are. Cracking Passwords: Bruteforce Attack with Hydra (CLI) xHydra (GTK) 7: 32 AM 1 comment Recently on Security StackExchange, I saw a lot of people asking how to use properly THC Hydra for Password Cracking, so in this post I'm going to explain how to install the command line utility, and also how to install the graphical user interface (GUI. Learn how to program a password cracker in python. This is purely theoretical, this will not help you get back into your Facebook or gmail account. GITHUB: h How to recover a lost zip file password. If you look at the supported modes there's some options (including the basic bruteforce) for cracking zip passwords. The blocks can be used to make the parts of the password fixed or permute differently from the rest. Disclaimer: I work for Maxotek who built these. Brute force is the most time consuming approach to password cracking. It should always be your last resort. Brute force password cracking attempts all possibilities of all the letters, number, special characters that might be combined for a password and attempts them. This is a 4step process, and while it's not terribly difficult to crack a WPA password with Reaver, it's a bruteforce attack, which means your computer will be testing a number of different. However, if the tester is unable to intercept the HTTP request, the tester should use brute force tools. Digest Access Authentication This value is used by the client browser in the calculation of a hashed password response. Lifewire Free Password Crackers for Windows, Word, and More. Backup Utilities Browsers Internet Video Audio Social Networking Most free Word password crackers are bruteforce password recovery tools. Free Word and Excel Password Recovery Wizard and CrackIt! are good examples of free Word. wordlist for brute force attack download, wordlist password, Word List Downloads, Wordlist Brute Force Attack, Word List Downloads. wordlist for brute force attack download, wordlist password, Word List Downloads, Wordlist Brute Force Attack, Word List Downloads [Collection Great Wordlist for Brute Force Attack. by do son Published November 23. Hacking Tutorial: Brute Force Password Cracking September 30, 2013 by Bryan Wilde One of the most important skills used in hacking and penetration testing is the ability to crack user passwords and gain access to system and network resources. The previous two attacks, Dictionary and BruteForce, enter a password into the locked program, the program then hashes the entry and compares the hash to the correct password hash. Rainbow tables compute hashes for each word in a dictionary, store all of the hashes into a hash table, retrieve the hash of the password to be cracked, and do a. Brute Force Attack is the most widely known password cracking method. This attack simply tries to use every possible character combination as a password. In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system. A common approach (bruteforce attack) is to try guesses repeatedly for the password and check them against an available cryptographic hash of the password. RainbowCrack is a hash cracker tool that uses a largescale timememory trade off process for faster password cracking than traditional brute force tools. Timememory trade off is a computational process in which all plain text and hash pairs are calculated by using a selected hash algorithm. Brute force attacks work by testing every possible combination that could be used as the password by the user and then testing it to see if it is the correct password. To see if the password is correct or not it check for any errors in the response from the server. This carries inference that RAR password encryption is one of the strongest between popular encryption systems in the context of brute force rate. Brute force password guessing attacks are very common against web sites and web servers. They are one of the most common vectors used to compromise web sites. To confirm that the brute force attack has been successful, use the gathered information (username and password) on the web application's login page. Account Lock Out In some instances, brute forcing a login page may result in an application locking out the user account. Hydra is often the tool of choice when you need to brute force crack a online password. Visit us to know more on password hacking tutorial. I am just coding some classic brute force password cracking program, just to improve myself. I've explained how my program works at the start of the code. Check some of those screenshots to unders The goal with your password is to make it hard for other people to guess and hard for a brute force attack to succeed. Many automatic password generators are. AxCrypt Brute Force Introduction and Background AxCrypt does not contain any backdoors. With a reasonably good password, its not practical to try all possibilities because it just takes too long time. Trying all possibilities, even when AES128 has been used instead of the stronger yet AES256, will take longer than the lifetime of the universe. In a traditional bruteforce attack, a malicious actor attempts to gain unauthorized access to a single account by guessing the password. This can quickly result in a targeted account getting lockedout, as commonly used accountlockout policies allow three to five bad attempts during a set period of time. During a passwordspray attack (also known as the lowandslow Blocking Brute Force Attacks. A common threat web developers face is a passwordguessing attack known as a brute force attack. A bruteforce attack is an attempt to discover a password by systematically trying every possible combination of letters, numbers, and symbols until you discover the one correct combination that works.
Related Images:
- How made s19
- Dr house ita 1
- John oliver s01e03
- Owl city maybe im dreaming
- Dark relic 2012
- Win 8 the rain
- Magix pro 5
- Secrets of the mary rose
- Google chrome apk
- Campbell biology concepts
- Maximum ride series
- Papa no iukoto
- English hardcoded subs
- Microhd castellano vengadores
- Barry white karaoke
- She is a devil
- Worlds End 002
- The great discovery
- After youve gone
- Red is the colour of
- Bitfield submerge mac
- 2013 hindi brrip 720
- The flash first
- Girl and panz
- New found glory mania
- New pure moods
- Black and never go
- Defiance 2008 nl
- Notes from the underground
- Return of the jedi 1983
- Projekt pro 2013
- How A stole christmas
- Scooby doo gree
- Cs6 design web premium
- Howard stern beetlejuice
- Beyond creation earthborn
- Carlton vs richmond
- Assassins creed no cd
- Big l big picture
- Jayden Jaymes Kagney Linn Karter
- Sexual fantasy kingdom vol 3
- Go for a ride
- Miles davis ascenseur pour lechafaud
- High exposure david breashears
- Tara Lynn Foxx Chanel Preston Mischa Brooks
- Sim unlock root
- Drop dead diva s04e08
- Nl subs falcon rising
- Under the cork tree
- Wale that way
- World war z 2013 dual audio eng hindi
- Glen campbell see you there
- Daredevil 02
- Blade of fury
- The blob french
- The walking dead nlsubs
- Bum rushed 2
- From 3 to 4 1080
- Katy perry greatest
- Del tha funkee homosapien automatik statik
- Star wars ios
- Hasbro family games
- Despicable Me 2 sub nl
- Convert to burn
- Digimon 3 ita
- Darkness falls english
- Revenge s01e11 720p hdtv x264 dimension
- Continued silence ep
- House of cards 720 s01
- Nightmare Adventures The Turning Thorn
- Wario wii mult
- The sims 2 keygen
- Need for speed underground soundtrack
- Life as a turkey
- L a story
- Flikken maastricht s06e01
- Web dl dd5 1 h 264 ntb